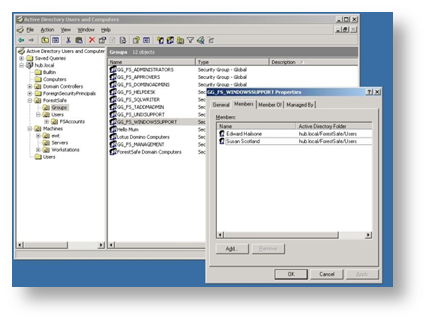
There is no user administration in ForestSafe. Authorisations are mapped from Active Directory group memberships
Features and Benefits
- ForestSafe users are only given read access to the database
- Only the account running the ForestSafe service has write access
- Kerberos SPNs are configured to send user logons details through the Web Application through to the ForestSafe Application
- Extremly secure, a completely transparent security model
Access control lists
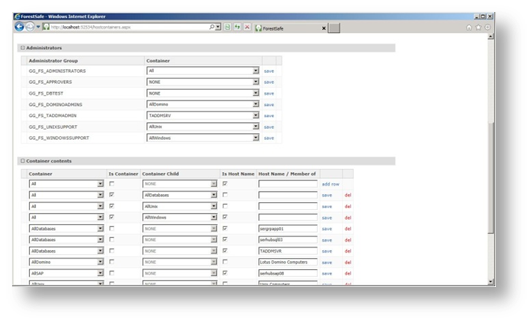
ForestSafe groups can be mapped to logical containers, the container are mapped to lists of computers. Using this system, any group of computers can be segregated and allocated to particular support team for example
Contents are always build dynamically, so careful container design means the system can run without any re configuration for years
Features and Benefits
- Administrator group access lists are managed by containers
- Containers may contain other containers or computers
- It is possible to put a single machine into a container
- It is possible to pattern match a group of machines into a container
- It is possible to map all members of an Active Directory Organizational Unit to a container
- It is possible to map all computers that belong to an Active Directory Group to a container
